Maintaining Access is the 9th step of the Kali Linux Penetration Testing cycle. It is the final step of penetration testing before the hacker reports their findings to the company they’re performing a penetration test for.
Once we are able to gain access to our target, it is natural that we have to be able to stay accessed to our target machine, at least until we finish our objectives on the target, should we go back to our target machines. We can choose to use the target system to scan and exploit our targets, or browsing through our target while also trying to remain undetected as in this stage, it can increase our vulnerability to detection.
There are many ways to maintain access, such as:
Protocol tunneling, which allows us to use a particular protocol to run or provide a service on another protocol that doesn’t directly support or provide said service. It sends a payload, or the data portion of a packet, to carry packets that provide the service.
How is this useful in ethical hacking? It lets us bypass protection in our target systems, such as firewalls and allows us to stay in stealth mode.
DNS tunneling is a method that is able to encode other programs’ or protocols’ data in the form of DNS query responses. Attackers can use this method to excerpt information from their target from its DNS records.
SSH tunneling is a method used to transport networking data from one machine to another through an encrypted SSH connection. It is commonly used to gain access on a remote shell.
Useful tools: dns2tcp, Ptunnel, Stunnel4
or using a Proxy server, where it acts as the middle server between the client and the web server. It is usually used when a client makes a request to another server, and the server returns with a response without it knowing who the client is. We can also use a reverse proxy, where clients make requests to the web server through the proxy, and the proxy returns responses as if they’re from the web server itself, which leaves the client not knowing about the origin server.
How is this useful in ethical hacking? It keeps our anonymity and it also lets us bypass restrictions such as filters and firewalls. Reverse proxies allow us to secure the real client behind the proxy since the server won’t know who the client is.
Useful tools: proxychains, 3proxy
Another way is to establish an end-to-end connection, creating a connection between the client and the server and has its functions stored at the endpoints of the network instead of the intermediate ones, such as gateways and routers. We can transfer files to the client from a remote server as well as executing command in the remote server.
Useful tools: CryptCat, sbd, socat
We can also make a backdoor PHP shell, where we can create a small PHP code and upload it to our target so we can use terminal commands from the browser. Once it is uploaded we are also able to access our target’s files and upload, download, edit or delete files.
This is an example of a web PHP shell:
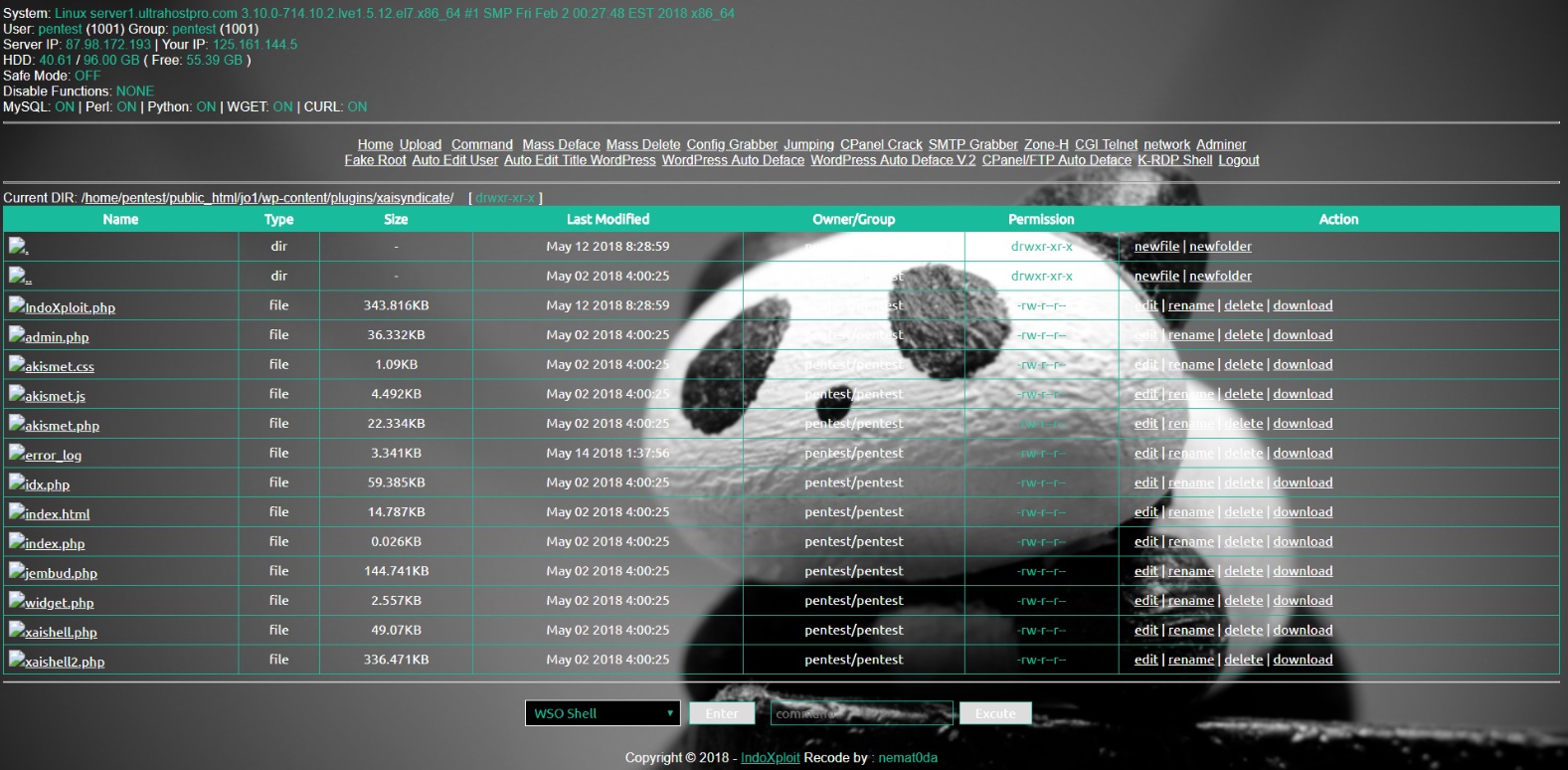
This shell is used on a wordpress website. We can do commands from the terminal through this shell using the Command page.
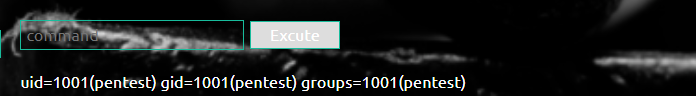
For example, we want to check our user ID:
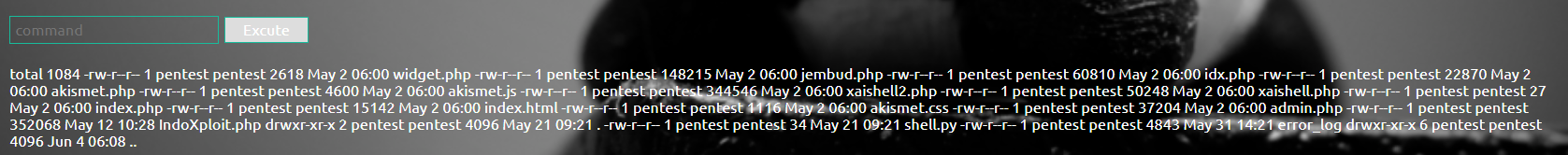
Or check what files are stored in the target:
We can also upload another file from the shell (I used another shell for this one)
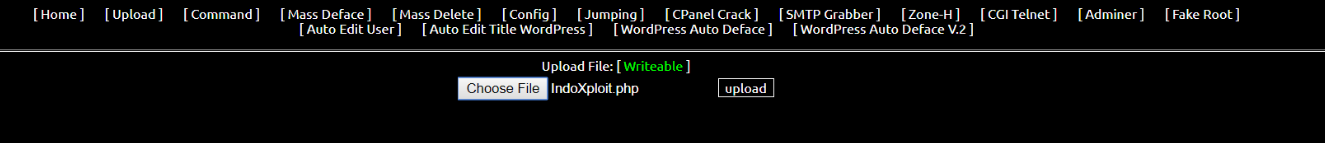
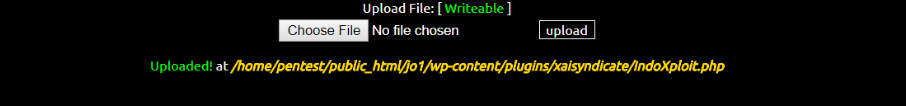
And just like that, it will be stored in the website.
If we want to have more stealth, it is advised that we insert our PHP code into an existing file and add a logic to avoid error, since shells usually get detected by our antivirus devices.
References:
https://en.wikipedia.org/wiki/Proxy_server
http://totaluptime.com/what-is-dns-tunneling/
https://www.ssh.com/ssh/tunneling/
