Port scanning is the act of systematically searching a computer’s ports. It is used to identify vulnerabilities as well as finding out which services are provided by a host.
These are the types of port scanning:
- SYN scan – Stealthy scan
- Connect scan – Completes the three-way handshake (method that is used in a network to create a connection between the local host and the server)
- NULL scan – Packet flags are turned off
- XMAS scan – FIN, PSH and URG flags are set
- ACK scan – used to pass a firewall
- FIN scan – Closed port responds with an RST packet
- UDP scan – Closed port responds with ICMP “Port Unreachable” package
Here are some tools that can be used for port scanning:
- Nmap
- Unicornscan
- Netscan Tools Pro
- Nessus
Now I will demonstrate on using the tools with the task given, which is to find the detail services in two hosts.
In this task I will try and use the nmap tool. If we type nmap in our kali linux terminal it will show a list of commands that can be used in the tool:
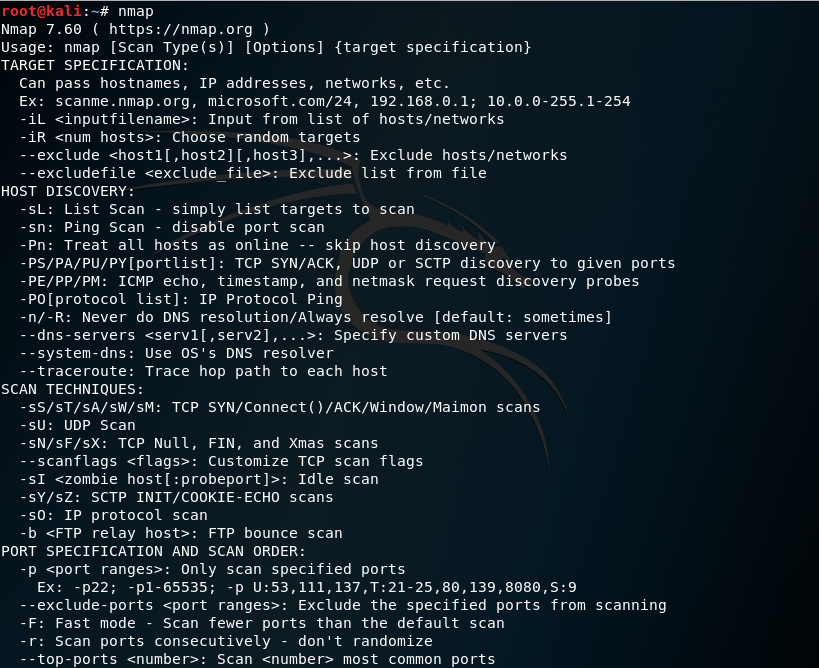
The first domain I will be using is host1.pentest.id; and the results will be like this:
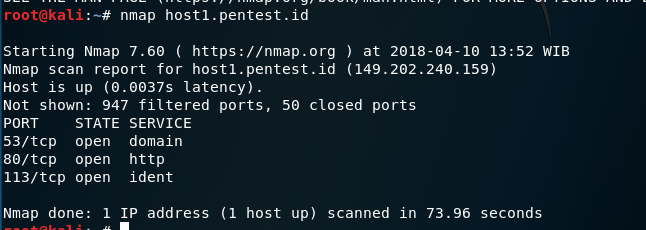
As you can see in the screenshot above, it will show its IP address and its number of ports as well as its details.
You can do a lot of things using this tool, for example we want to find out about its operating system:
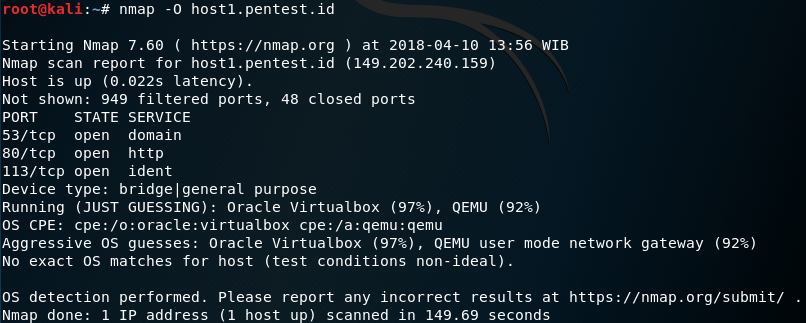
The nmap -O command is used to scan and guess the OS that is used in the website.
Now I will demonstrate one of the port scanning methods using this tool.
For example, I want to do a SYN scan on host1.pentest.id.
First, what we need to do is open our Terminal as well as our Wireshark.
In our Terminal, we need to simply run the command shown in the screenshot below:

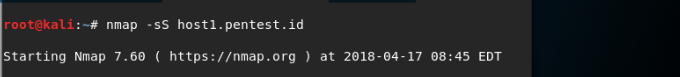
Nmap will start the SYN scan. The results will be shown in Wireshark in the screenshots below:
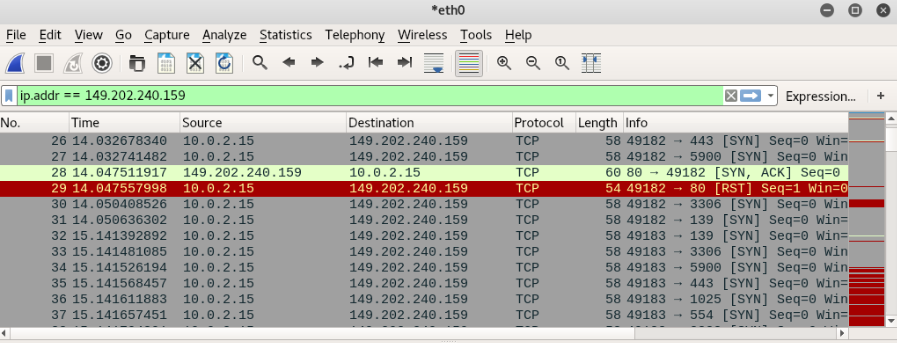


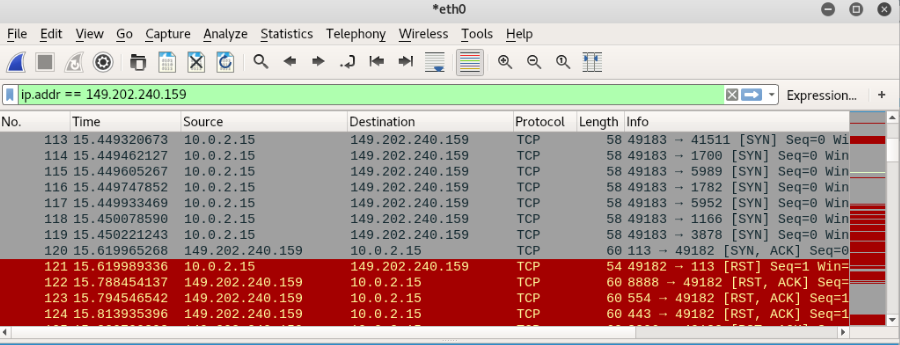
From the results above, we can figure out which ports are open and which ports are closed. If the port from our target IP sends back a [SYN, ACK], it means the port is open. Ports that send [RST, ACK] responses are closed ports.
References:
https://www.webopedia.com/TERM/P/port_scanning.html
