On this post, I will talk about target discovery and finding out old versions and/or archives of a website, as well as finding out the real DNS of the server.
These are things of the past, but why do we need to look for old records? Old records can be used to find vulnerabilities, such as old scripts, that contains vulnerable code. In some websites, old servers are still used and it is easier for us to breach the website.
Here are some tools that can be used:
- dnstrails
- robtex
These tools can be used online, and it is fairly easy to use. Let me demonstrate on using these tools.
First I will use dnstrails. This is how the website looks like:
What we want to do here is to find the historical DNS data for a website or domain. For example, I will use the domain pentest.id.
The results will be shown like this:
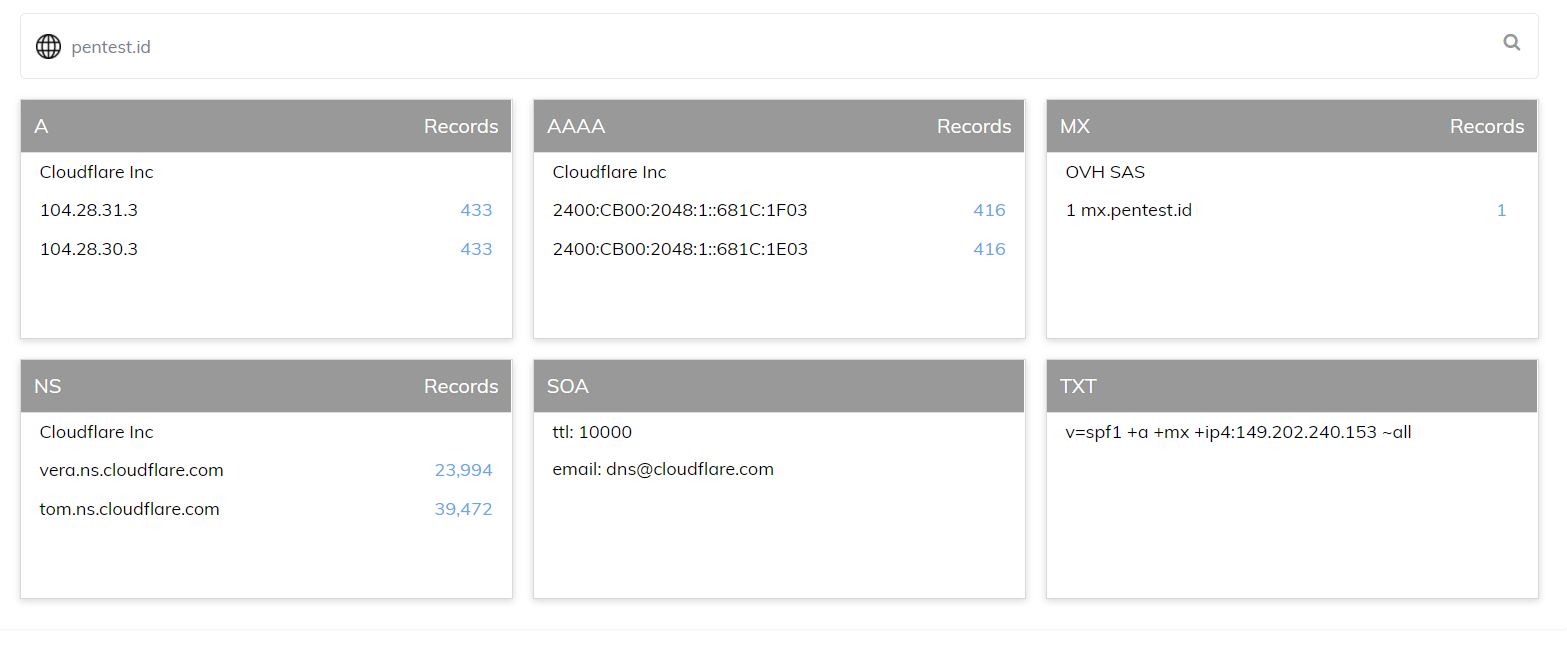
It shows the IP addresses used, the host that is used to provide the website and when it is first seen and when it is last seen.
It also shows details such as the whois registrant (I used a different domain for this):

The second tool I will use is robtex.com. The domain I will use to demonstrate will be the same, which is pentest.id.
The results should be like this:
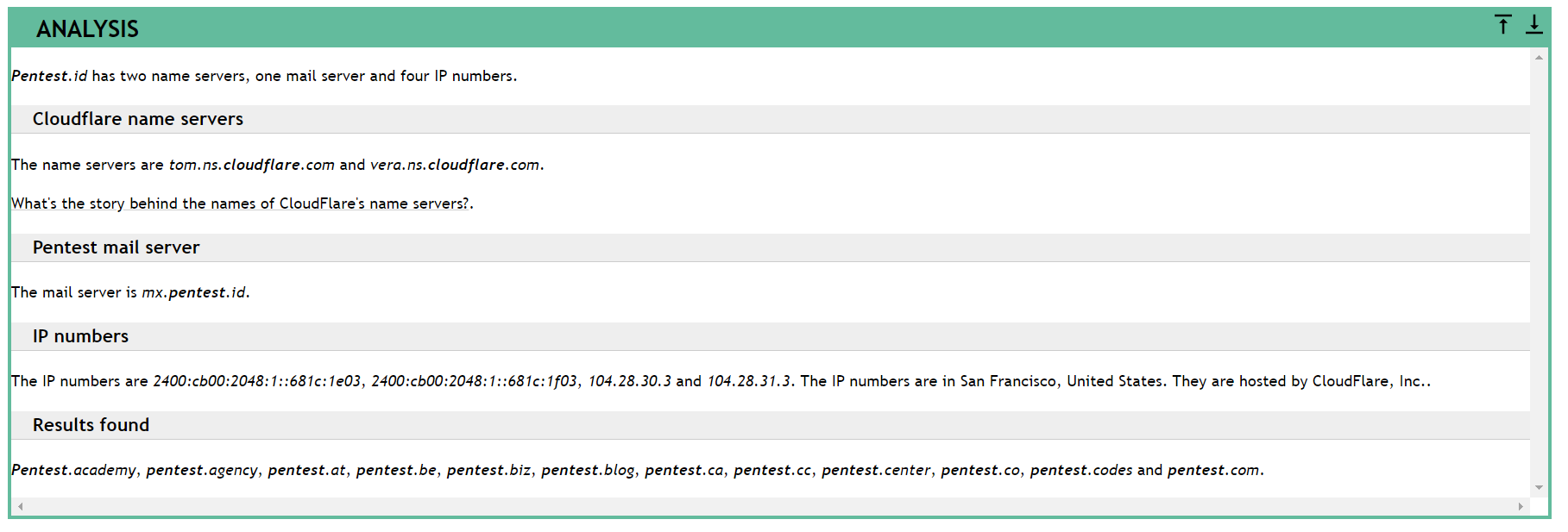
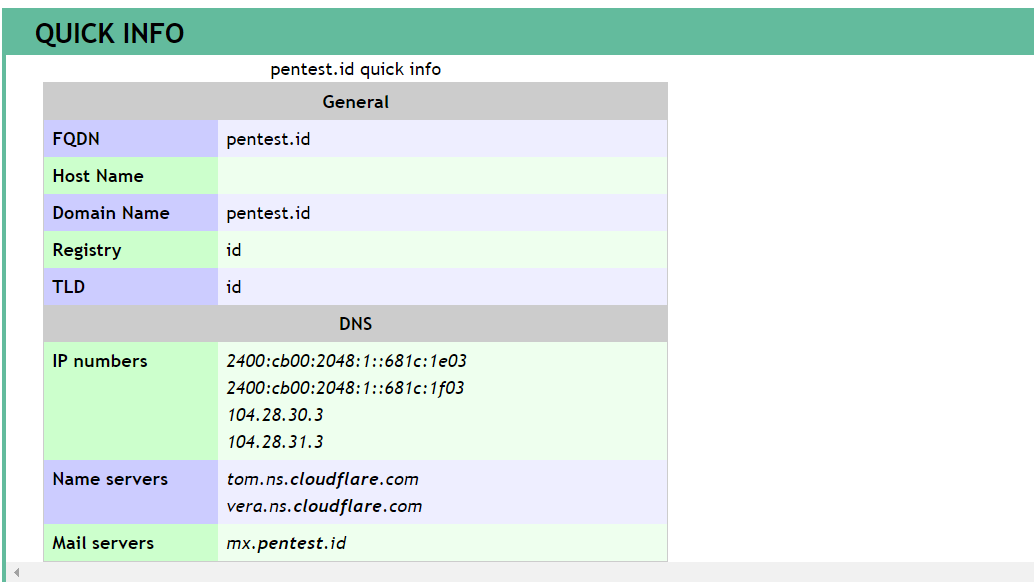
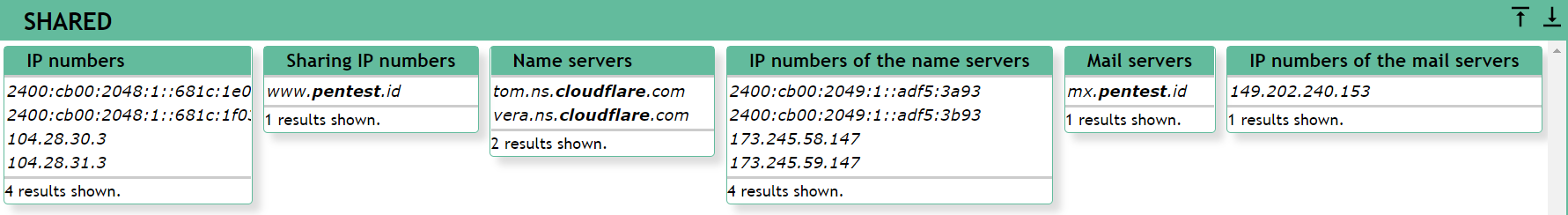
As you can see in the screenshots above, the results are somewhat similar to the dnstrails results. It shows information such as the real IP addresses, the host servers used, the IP addresses of the servers, as well as its mail servers.
There are other methods that we can use to find information such as the real IP addresses, such as using the outgoing e-mail addresses of the target. The target may also have features that contain vulnerabilities, and we can use that to connect to the IP address that we want (such as wordpress’ xmlrpc). We can also create our own script manually.
