On this week’s session I learned more about information gathering, and tried to gather information from certain websites. using Kali Linux’s Maltego. I also learned about zone transferring, as well as other tools and search engines that I can use to find specific things instead of using Google.
Zone transferring helps us see all of the hosts that is in a network, and the network diagram of an organization. Zone transferring has its own tools: Dig and Host. The Dig command sends queries to the DNS name server so we can gather information such as host addresses, and the mail exchange services they use.
For example, I used the dig command on the website pentest.id:
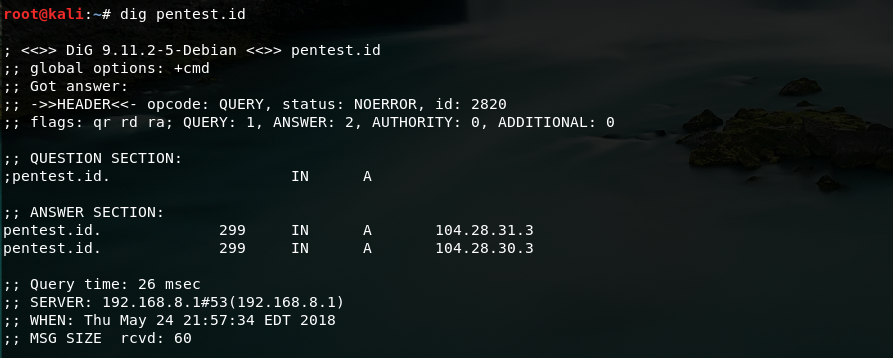
This is the results of the default query. It shows the IP address (A) of the website.
The Dig command lets us do valid DNS queries, such as finding out the e-mail servers or name servers of the website.
For example, I want to find out the mail servers that the website used. We can just type in this command:
dig [website] mx
The results will come out like this:
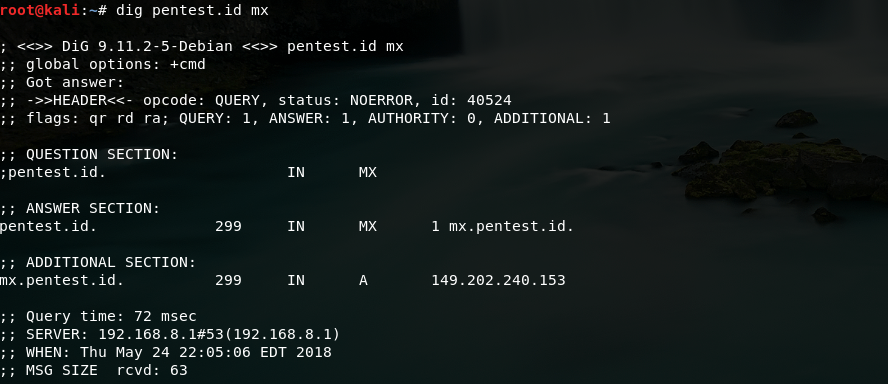
It shows the mail addresses that the website is using.
Next, I will demonstrate the Host command. The Host command, just like the Dig command, can also be used to perform DNS lookups.
First I will do the default command:
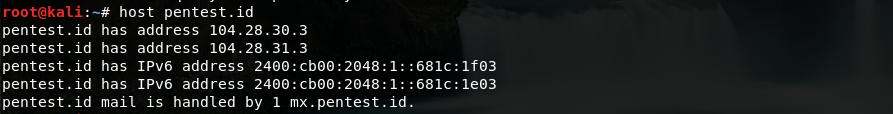
Just like the Dig command, the default Host command shows the IP addresses of the website, but in this one it shows both IPv4 and IPv6 addresses as well as its mail servers.
I am going to try to use another command to find a specific answer, such as its name servers, using this command:
host -t ns pentest.id

The results show the name servers that the website used. In this case, we can see that the servers that the website is using is Cloudflare
There is also the whois command, which is also used to gather information. The whois command is used to search an object in a WHOIS database, which is a query and response database that stores users that are registered in an internet source, and other forms of information.
Now I will demonstrate information gathering using the WHOIS command.
For example, I want to gather information on a website, let’s use pentest.id:

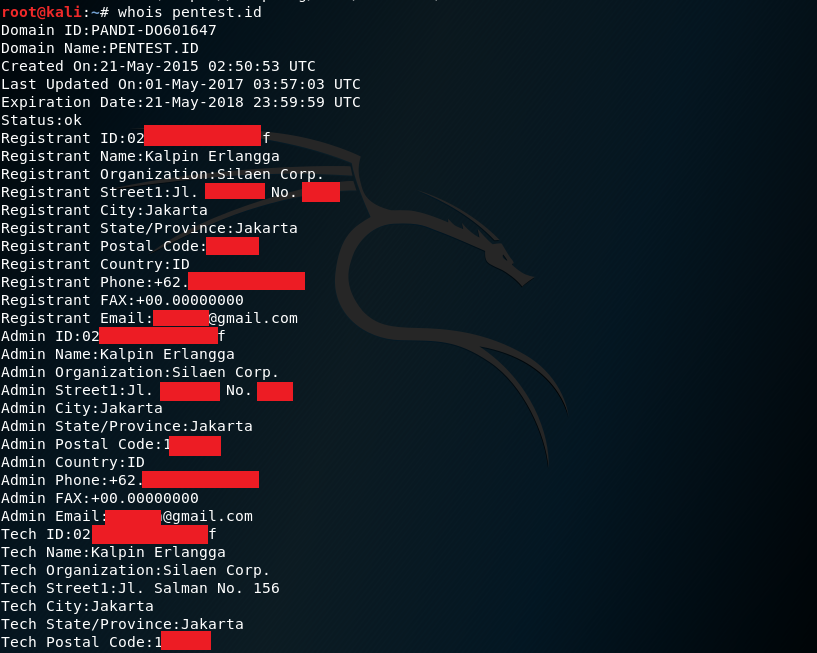
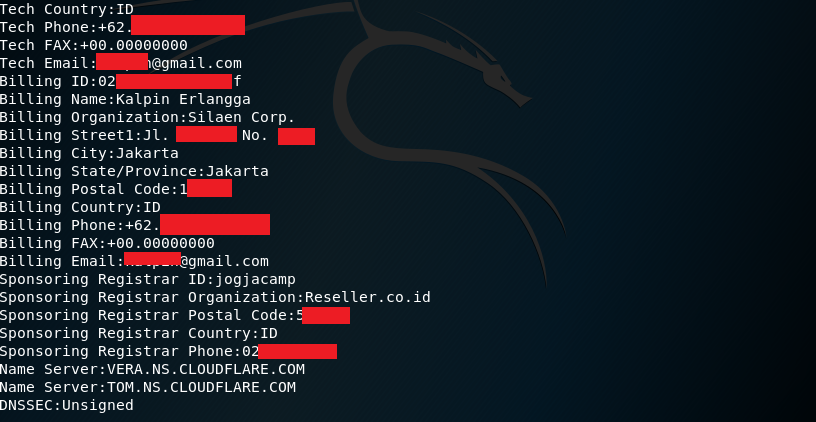

As you can see from the screenshots above, the whois command shows the details of the administrator of the website as well as its registrants. It also shows the billing details of the website, its sponsors and the servers used for the website.
References:
https://mediatemple.net/community/products/dv/204644130/understanding-the-dig-command
